Secure and Private Browsing
 So, after the Browzar fiasco, I went looking for a simple, secure, private Portable Browser that I could use to surf the net in strange places with.
So, after the Browzar fiasco, I went looking for a simple, secure, private Portable Browser that I could use to surf the net in strange places with.
What I found is TorPark. It's a modification of Portable Firefox (a version of Firefox for running portably on USB sticks) with Tor built in. TorPark takes Portable Firefox and preconfigures a number of Privacy-related Extensions.
The more people who are using Tor at any one time, the more anonymous it is. It's basically a giant, distributed Proxy Server. Everyone gets pages for everyone else.
I tried it, and while it's slower of course than going directly, I saw that my traffic was routed through a number of countries, just by repeatedly visiting WhatIsMyIPAddress.com.
This seems like a much safer and reasonable alternative to Browzar if you're in the market for a portable, private browser.
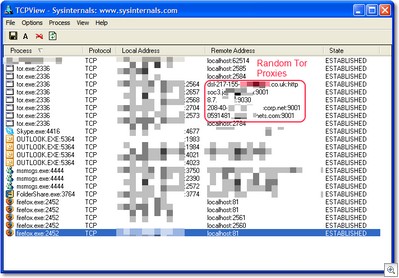
Here's TCPView running while I run TorPark. Notice Firefox only talking to localhost while Tor.exe connects to random Tor proxies.
I also run my installation of TorPark on a TrueCrypt encrypted Traveller Disk on my USB device. I talk about TrueCrypt in this post.
About Scott
Scott Hanselman is a former professor, former Chief Architect in finance, now speaker, consultant, father, diabetic, and Microsoft employee. He is a failed stand-up comic, a cornrower, and a book author.
About Newsletter
[)amien
This is all well and good, until, as chance would have it, my connection is used for some pervert to deal in child porn. Or plot a terrorist attack. Now, I don't rightly care what you use my connection for in theory. That's why I'm donating the bandwidth to Tor. But, as we've seen in a lot of DMCA/RIAA John Doe cases, I might actually be held responsible for the content accessed from my IP address.
IANAL, but I worry about the liability of operating a Tor server. At the very least, it gives the fuzz a good excuse to kick your door down and confiscate all of your hardware (thank you, Patriot Act).
People should not fear their government. Their government should fear them. This is my ideal, and I'm sticking to it. That said, I really have no desire to stand tall before the man. Am I totally wrong in my thinking here? Is there any case precedent to help me feel safer about hosting a Tor server in the US? Or is this something for which I will have to rely on my freedom-loving overseas brethren?
Of course, I posted my last comment before I read what Jon Galloway recommended:
<quote>
5.2. I'd run a server, but I don't want to deal with abuse issues.
Great. That's exactly why we implemented exit policies.
Each Tor server has an exit policy that specifies what sort of outbound connections he will allow from his server, and what sort he will refuse. The exit policies are propagated to the client in the directory, so clients will avoid picking exit nodes that would refuse to exit to their intended destination.
By default, your server allows access to many popular services, but restricts some (such as port 25) due to abuse potential. You can edit your torrc to make your exit policy more or less restrictive. If you want to avoid most if not all abuse potential, set it to "reject *:*". This setting forces a "non-exit" operation. Nobody exits through your node, only direct connections to other nodes will be established.
</quote>
Okay... So I can block individual ports. That's helpful, since it keeps spammers out. Still doesn't explain how I might prevent being used for behavior that could make me criminally liable short of setting a non-exit policy. Truthfully, I realize that it's not really a realistic expectation, and certainly is not in the spirit of Tor. Guess my options are:
1) Run a server and run a risk of showing up in subpoenaed IP logs for something I didn't do
2) Run a server and set it a non-exit policy
3) Don't run a server and just leech bandwidth from the Tor network
Comments are closed.

So using TOR with Privoxy gets you about as close to invisible on the internet as you can get. I've also heard of people tunneling SSH to their home proxy using TOR and using Squid at home to pre-fetch pages and download their email if they are using a public hot spot. I can't think of anything more secure than that other than using a Sneakernet to transport the packets.