Using Code Signing Certificates to sign downloaded MSIs and build reputation with IE9 SmartScreen
First, let me start that if you want a lot of people to download something, make sure that the words "HTML5," "Support" and "Update" appear in the title. I'm sure if the folks that are making Diablo 3 called it "Diablo 3 HTML5 Support Update" that a metric buttload more people would download it.
That said, a bunch of folks in the Web Platform and Tools team created the Web Standards Update package with HTML5 Support for the Visual Studio 2010 Editor.
This Web Standards Update is something that anyone in the community could have released, just extending Visual Studio in a standard way. Like many other (most) extensions in Visual Studio Extension Gallery, it was not "signed." It was not a formal project done by Microsoft. Ratherthis was something that a bunch of us did for the community in our after work hours. The only reason why this got in spotlight was because press caught the wind of it having HTML5 and CSS3 support.
Certainly a lot of people wanted it because in 4 days it's now the #1 most popular thing in the Visual Studio Gallery. Take that NuGet! ;)
Here's where the trouble starts. Then, it was written about in the press as if it were a "gaffe." I admit that we (mostly I) did a lousy mediocre job of making it clear that this update was a "community update from the inside," as it were. It's not official, but we're hoping support like this will make its way into the next version of Visual Studio.
When you downloaded the MSI installer with IE9, as with all MSIs that aren't signed, you get a message like this:
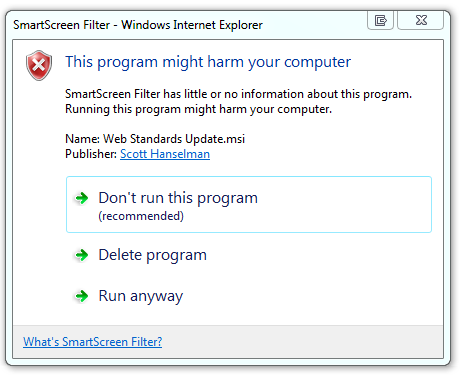
And that's normal and quite lovely. Then we see this scary red bar (this is a shot from another gallery item):
This is the IE9 SmartScreen system warning us, rightfully so, that this is not something downloaded all the time. In fact, this is a really useful feature of IE9 and is fairly unique amongst the browsers so far. It's using some special sauce (some hash, some math, some metrics) to make a non-biased judgment about this download. Even though it's coming from a Microsoft.com website it doesn't matter. SmartScreen is unbiased. It's never seen this before, and it's not trusted.
UPDATE: Looks like as of my test just now that SmartScreen now recognizes our download as safe!
At this point, if I click Actions, I see this. (Yes, I realize these screenshots aren't all up to snuff).
_9a12330c-2264-49f0-8d29-bbd55f7ffb0a.png)
In fact, for most people, they can't even click "Run Anyway" yet. They'll have to click More Options to see the Run Anyway button. (If I am a developer-type and click More Options all the time, presumably I either know what I'm doing, or I like to live dangerously and the More Options choice will stick open after several downloads. It'll save me a click, but all the other warnings remain.)
As the publisher, we have a few choices. We could sign the binary file (the MSI) with the Microsoft code certificate. However, that requires a big manager to sign off and says explicitly that Microsoft is releasing this code officially. It's a big deal. This wasn’t an official release and as such, we can't sign it as Microsoft. A code signing certificate guarantees that a file hasn't been tampered with and that a known and verified organization or individual stands behind it.
Eventually SmartScreen would figure out that our MSI was OK, but we have no way of telling how long that would take. Could be weeks, months, it all depends. Regardless, the right thing to do is to sign your code, even if you are an individual or small company. For example, if I download Eric Lawrence's Fidder or Rick Brewster's Paint.NET, they are both signed and I can see their names in the User Account Control (UAC) dialog. I can click and view their certificates and know I'm downloading a file that has someone vouching for it.
Be sure to check out Eric Lawrence's excellent post on Authenticode Code Signing. It's extremely detailed and worth your time.
Getting a Code Signing Certificate
I got a Code Signing Certificate from InstantSSL.com. There's many options, they are one. It's spendy, $180 a year, or $166 a year if you got for 3 years, but I can use it for other stuff.
There's a few gotchas in the process, no matter who you pick.
- Use the same computer, same OS, and same browser (preferably IE, for this, no joke) when you sign up for the certificate. That's because half the certificate (a cert request cert) comes down when you request a certificate and they match them up when you actually get the certificate.
- Have P.O. Box, corporate address or ask them via tech support to remove your address. Otherwise your full details may get embedded in the cert.
- You'll need to prove who you are. More on that now.
You'll need to prove you are really you. I needed to give their verification people a copy of the first page of my passport, driver's license, two utility bills, including phone whose address matched my credit card's address, AND they called the phone number on my utility bill to confirm it was really me. It's non-trivial, it takes a while, and they aren't screwing around. Good for you, the consumer, hassle for me, the producer. Still, good stuff.
_3.png)
When my cert shows up, I need to Export it and save it in a safe place with all its details and a strong password. It's unique and should be protected.
Signing Code
The actual signing, once the cert shows up is not too hard. Here's a command line used with the signtool.exe that came with Visual Studio. You can also download it separately.
C:\DEV> signtool sign /t http://timestamp.comodoca.com/authenticode /f "C:\DEV\HanselmanCODESIGNINGCERT.pfx" /p SecretPassword '.\MySpecial.msi'
Done Adding Additional Store
Successfully signed and timestamped: .\MySpecial.msi
When someone tries to download the new signed MSI, they see this slightly less scary yellow bar. What? I don't get a free pass for signing my code?
Well, just like getting an SSL certificate doesn't make me a bank, getting a Code Signing Certificate doesn't make me more trustworthy.
- SSL Certificates for HTTPS guarantee privacy, not trust.
- Code Signing Certificates guarantee identity, not trust.
- It guarantees it's me, but you have to decide if you trust me.
If you click Actions now, you'll see my name as the Publisher, and you can validate the certificate and decide if you trust me. But SmartScreen doesn't trust me yet. Why?
That's because my Certificate, unlike the Microsoft one, hasn't built up a reputation*. The "Scott Hanselman" code signing cert will have to earn trust, just as Rick Brewster and Eric Lawrence and every other signed shareware or freeware author has built trust. But, having this MSI signed means you now that I (and Mads, and Vishal, and the folks working on this MSI) stand behind it. Hopefully soon (some # days or weeks vs. downloads?) SmartScreen will trust us also, and this will make future projects I sign be trusted faster. At that point, my signed code will be trusted and SmartScreen won't frighten you with this download.
Remember also that code signing certificates and the Windows experience and UI for running signed MSI and EXEs is a separate from SmartScreen. They work together and compliment each other though. Learn more about SmartScreen on their team blog or their FAQ.
Hope this helps! Surf smart, and think about what you download and who you trust.
* Now it appears that SmartScreen trusts me!
About Scott
Scott Hanselman is a former professor, former Chief Architect in finance, now speaker, consultant, father, diabetic, and Microsoft employee. He is a failed stand-up comic, a cornrower, and a book author.
About Newsletter
I will not sign my code until Microsoft starts providing free (or very cheap) signing certificates, which they should do if it really is so beneficial. Small hobbyist developers simply cannot afford these prices. These certificates are simply a money-making device and nothing more at these prices.
To punish small developers with limited resources like this is going to hurt in the long run. It is after all the wealth of applications that makes Windows what it is.
[Sorry for the double post]
https://secure.ksoftware.net/code_signing.html
"LOWEST Price Guaranteed!
If you find a lower published price for a
comparable code signing certificate,
email in and we'll beat it."
1 year - $99.00
regards, gerry (lowry)
Really! Now is that practical. Maybe in 1980 but not today.
From the reference link (http://blogs.msdn.com/b/ieinternals/archive/2011/03/22/authenticode-code-signing-for-developers-for-file-downloads-building-smartscreen-application-reputation.aspx) under the section "Best Practice: Time-stamping"
"It turns out that not all publisher certificates are enabled to permit timestamping to provide indefinite lifetime."
AND
"It also appears that some CAs do not provide SPC and PVK files, instead providing the certificate in a different format."
Really! Now is that practical.
(would love to see a comment feed for each of your blog posts... at least chrome doesn't show me one)
BOb
"...this amounts to guilty until proven innocent and feels like a slap in the face..."
I have to agree. The first time I read about Smart Screen, I thought it was a terrible idea, and nothing I have heard in the meantime has given me cause to change my mind. Popularity != trust, and lack of popularity != lack of trust. Smart Screen is conflating two completely orthogonal ideas in a way that will be detrimental both to publishers and consumers.
Scott, you may be lucky enough to be working on projects that tens of thousands of people or more are going to want to use; you can develop "trust" quickly. Most of the rest of the world isn't so lucky.
CN = UTN-USERFirst-Object
OU = http://www.usertrust.com
O = The USERTRUST Network
L = Salt Lake City
S = UT
C = US
Wondering why it doesnt read as "COMODO Code Signing" as I see here at scott's screenshot.
Any ideas?
David - SmartScreen is not about # of downloads, it's about time, and virus scans, and reports of evil (or not) and all sorts of special sauce. Even if you don't use a Cert, it will eventually notice you and realize you're not bad.
PilotBob - Links to my Comments RSS use the standard markup for comments and there's also a link at the bottom of each post.
DaveWill - Ya, but then I just export it and store it in DropBox, so I'm not sure what the problem is?
As a power user or developer I will generally make up my own mind about what to install. I know what's going on behind the scenes and I'm fine owning the problem and rebuilding if I get it wrong. More casual users might be so scared by the dialogs that they just walk away. For a publisher still trying to build up trust with SmartScreen that's really harsh. Even a few lost users is a big deal at that level.
Makes a stronger case for more trusted (perception, not logical trust) platforms such as tablets and browser based solutions. Installing anything on the desktop has some casual users too petrified to proceed. They'll reject a desktop solution and favor a web-based solution purely based upon the fear of the UAC warnings. I've witnessed this with friends, family, and many non-technical people in decision making positions at large companies. There is a general desktop-app resistance building as a result.
From the SmartScreen FAQ:
"SmartScreen Filter checks files that you download from the web against a list of reported malicious software sites and programs known to be unsafe. If it finds a match, SmartScreen Filter will warn you that the download has been blocked for your safety. SmartScreen Filter also checks the files that you download against a list of files that are well known and downloaded by many Internet Explorer users. If the file that you're downloading isn't on that list, SmartScreen Filter will warn you."
It sure sounds to me like, in the absence of explicit evidence of evil, SmartScreen uses download popularity as the metric of trust. Are you saying that's not the case?
DaveWill - Ya, but then I just export it and store it in DropBox, so I'm not sure what the problem is?
Your article was focused (it didn't cover the gammit of digital signing) and well thought out. Yet still in this focused window of digital signing we see that the process isn't very friendly. I had never heard of the fact that the machine used on day 1 of the process mattered on day 2 before. This just re-enforced my belief that we need to come up with a different way to skin this trust problem.
Now if IE says not to download the software & user does not downloads the software, it is really difficult to get trusted by SmartScreen Filter
This is like round robin and if Microsoft would have designed in a better way, then the SmartScreen filter could warned users appropriately about only softwares that are malicious and software vendors who put efforts, would not have suffered.
From the post it seems like the certificate gains trust and once certificate gains trust (SomeHow) software applications signed by the certificate would not be marked as harmful by SmartScreen Filter
This is major issue! The checking is done on the certificate level, on its serial number, not the entity it was issued to.
So the only way to keep being trusted is to purchase a certificate valid for x number of years. This will cost a lot more money. But the main issue is that SmartScreen should check reputation based on the one being issued the certificate, not the individual certificate.
Comments are closed.

While I certainly understand the motivation behind SmartScreen, I think this is detrimental to small developers like myself. I develop niche enterprise type software for a small number of customers. I have been signing my code for several years and have been in business for over 14 years, but now my customers will need to go through this process which in turn makes me look unprofessional. My bottom line gripe is that this amounts to guilty until proven innocent and feels like a slap in the face to those of us who have developed for Microsoft platforms for so many years.
I've written a more extensive reply to the team and they were considerate enough to respond to a comment on their blog. I even offered suggestions on how I think this could be handled more fairly. As I understand it the Windows Logo program is also helpful in establishing reputation, but unfortunately is not a fit for any of my current projects.
I'd be happy to share more of my thoughts offline. SmartScreen may be a well-intentioned change, but it has unfortunate consequences to some us.