Saving and Retrieving Browser (and other) Passwords
The security balance is always user convenience vs. absolute security. You want security? Disconnect your computer from the internet. Don't save your passwords. Use multi-factor authentication. But that's not reasonable.
- Browsers let you save the contents of Forms that you fill out, including passwords.
- Some browsers sync those settings/histories/passwords to other computers with that browser running, if you are signed into a service with a master password.
- Those passwords need to be stored somewhere locally, and they need to be retrieved by the browser (who is not running as administrator) so that the browser can fill out your form for you.
- Someone writes code to retrieve those passwords.
- If you, running as you, the user, can access those passwords, than other code running as you, the user, can also access them.
If you don't like this, don't save your passwords.
I think the concern (I know I was concerned) about the recent hubbub about browser security is the feeling of casual disclosure. It is uncomfortable when it seems easy to get your passwords. But they are still there.
Remember the 10 Immutable Laws of Security, specifically #3.
Law #3: If a bad guy has unrestricted physical access to your computer, it's not your computer anymore.
Every password vault has this behavior. If your passwords are stored locally, they may be encrypted but they are stored with reversal encryption.
Is this a security problem/bug/flaw? No. You saved your passwords as the user and they can be retrieved by code running as the user.
Here's some just a few lines of code to retrieve and dump your Windows Password Vault on Windows 8.
using System;
namespace DumpCredentials {
class Program {
static void DumpCredentials(Windows.Security.Credentials.PasswordCredential cred) {
Console.WriteLine("Resource: {0}", cred.Resource);
Console.WriteLine("UserName: {0}", cred.UserName);
Console.WriteLine("Password: {0}", cred.Password);
}
static void Main(string[] args) {
Windows.Security.Credentials.PasswordVault vault = new Windows.Security.Credentials.PasswordVault();
Console.WriteLine("{0}", vault.GetType());
foreach (var cred in vault.RetrieveAll()) {
cred.RetrievePassword();
DumpCredentials(cred);
}
}
}
}
Feel free to change your browser settings if you like to not save your passwords, or consider other password vaults like LastPass, KeePass, or 1Password.
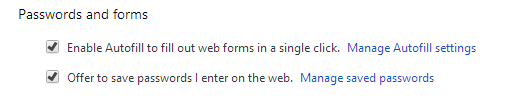
Chrome
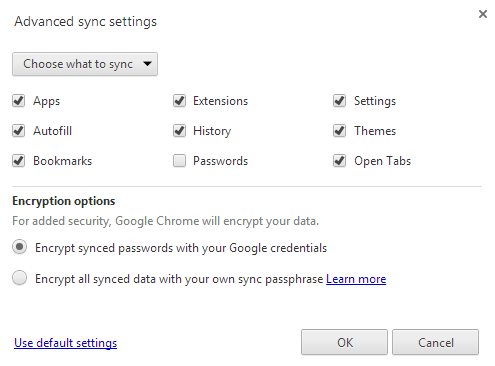
...and also...
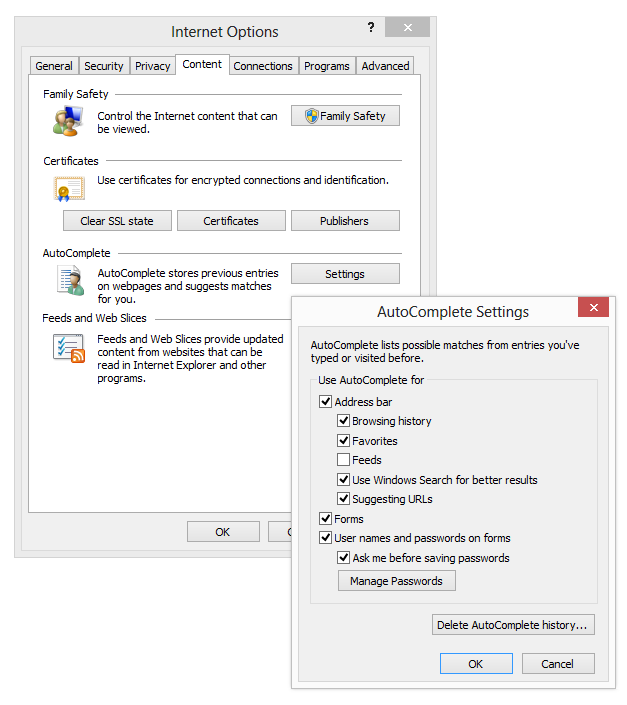
Internet Explorer
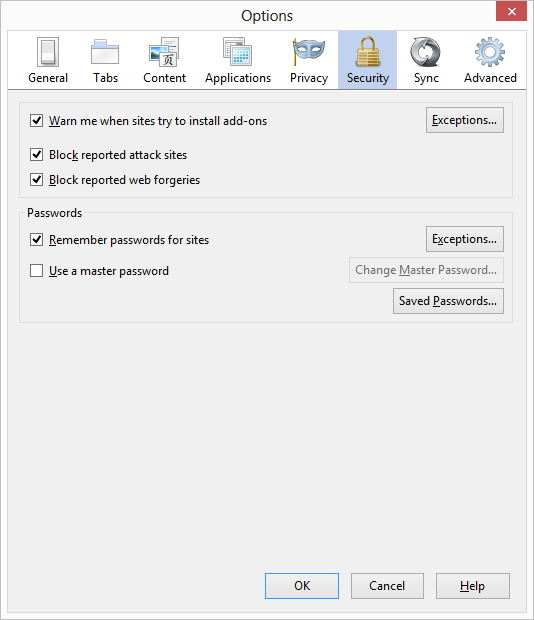
FireFox
The code to dump Windows 8 Paswords is here. It will compile with VS2012 on Win 8. If you just want the EXE to run, download it here.
About Scott
Scott Hanselman is a former professor, former Chief Architect in finance, now speaker, consultant, father, diabetic, and Microsoft employee. He is a failed stand-up comic, a cornrower, and a book author.
About Newsletter
I think I read the same article you did and I comment I heard quite often was 'all browsers do that'. I don't think that's the right approach - I think you could make a solid argument that all browsers are wrong in this regard. I think they should all enforce a master password at the very least.
That means they need to be kept somewhere where code running as the user can decrypt them.
Sure, it doesn't solve the problem that if the browser stores my password encrypted that another user can't insert that encrypted password into their browser and authenticate to that site. It would fix a little bit of the shared password problem though. If I used the same password for everything, they would all have different encrypted versions (remember the salt!) and wouldn't give that away.
$vault = new-object "Windows.Security.Credentials.PasswordVault" @()
Write-Host $vault.GetType()
$vault.RetrieveAll() | % { $_.RetrievePassword(); $_ } | format-list @(Resource, UserName, Password)
and the concluding pipe into format-list probably isn't necessary given the automatic formatting (warning -- untested since I'm not on a Win8 machine ATM)
However, not to be alarmist or sound like a paranoid psycho, but entrusting ALL my passwords to one "jackpot"? Isn't that even worse? I personally prefer all the recommendations you mentioned above as well as multi factor authentication so that even if my password is compromised I still have one more level of security.
It would also be nice to get an alert every time any of my accounts is accessed I get an email or some kind of alert (sms?).
I think we will all be more secure when security is reduced to having something (a phone, a chip, etc) or being somewhere in person (biometrics). This would be more convenient.
Concerns like this also show the advantage of curated appstores and application certification. because if our "trusted devices / systems" are compromised, what do we have left?
That said, I am not speaking from the perspective of having some thing to hide rather from that of someone trying to have some privacy and guaranteed safe uncorrupted storage of my digital life.
Cheers
The last thing I want, if I have selected a complex password, is to have to click "forgot password" and then have to update it in every device I have entered it in.
What I would rather do is: click "Show" in my browser or password vault of my choice, see what the password is, then enter it in the new device.
I'm sure it is exciting to get riled up about how "unsecure" everyone else is. In my case, this is much better for my security than if I used the same password everywhere or had to change it everywhere each time I forgot it and needed to enter it in a new program or device.
My security measure is to always lock the browser whenever I leave my machine. I even do this at home. If you want to use my machine, you will need to use your own credentials to do it.
http://www.wikihow.com/Create-a-Password-You-Can-Remember
Combine one or more methods like these which incorporate some data specific to a given web site and you can consistently re-generate strong and unique passwords, as needed. There is of course a vulnerability to spearphishing if a sufficient number of passwords become compromised for the attacker to reconstruct your mental algorithm.
-danny
if I use LastPass, KeePass, or 1Password etc, How can I ensure my security?.
Some applications respond to Windows events notifying that you've locked your system or that someone else has logged on or connected to their session. RoboForm, for example, will lock your password vault when someone else has logged on or when you resume your system from stand-by or hibernate. TrueCrypt exposes similar behavior; it will dismount TrueCrypt volumes when the same events occur.
Comments are closed.

I may be biased, but it seems to me that LassPass runs in the browser (urk) and 1Password is non-free (in both senses). Again, I don't want to start a flame war over password managers.
My $0.02