Outlook 2007 Beta introduces its own Feed URL Protocol. Ew.
(This discussion refers to Outlook 2007 Beta 2 Technical Refresh)
 I'm really not sure how I feel about this.
I'm really not sure how I feel about this.
There was a big discussion about if the feed:// protocol was needed. Personally I've always said I think it IS needed while the RSS Team at Microsoft disagrees.
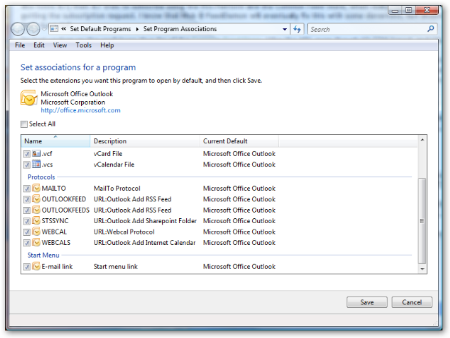
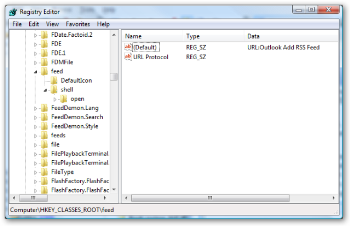
However, I just noticed that not only does Outlook store it's RSS in the PST (and syncs with the Common Feed Store, which we already knew), but it also registers two new "Protocol Handlers" explicitly for handling RSS feeds - they are OUTLOOKFEED:// and OUTLOOKFEEDS:// with the latter including an "S" for secure feeds.
This doesn't seem exactly fair or consistent. I understand that an enterprise, especially one using SharePoint would want to have folks subscribe to a feed directly into Outlook. However, not only is Outlook creating these new pseudo-protocols that are Outlook-specific, it's also taking over FEED:// as well. We'll see if there's changes in the next RC.
That doesn't seem fair. What if RssBandit started using RSSBANDITFEED://? Of course, any of these aggregators can try to take over OUTLOOKFEED://, although Outlook will likely bork. However, it's the very existence of this custom psuedoprotocol that I find offensive, it doesn't matter it can probably be disabled.
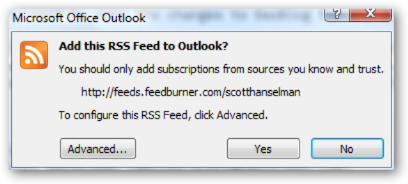
ASIDE: For some reason FeedDemon always warns me that it isn't the default feed reader (i.e. it's not associated with the feed:// protocol, and even though I want it to be the default aggregator, it keeps prompting. This might be a Vista-specific administrative thing, but I suspect Outlook is taking over feed:// also.
 You can test these various protocols on your machine by trying each of the following links:
You can test these various protocols on your machine by trying each of the following links:
- My feed using FEED://
- My feed using OUTLOOKFEED://
- My feed using OUTLOOKFEEDS:// (won't work, I'm not secure)
- My feed using HTTP://
Also, right now, if you click an RSS Feed while running FeedDemon (just using FeedDemon as an example application that eats RSS but also hosts IE7) then IE7 tries to subscribe using the RSS Platform and the Common Feed Store, when really FeedDemon should be getting the subscription request. I know that Nick @ FeedDemon will eventually fix this with some cleverness, but should he really have to?
I'm just unclear on the usefulness thus far of the Common Feed Store. I like the API (inside msfeeds.dll and a few other places that you'll get quietly when you get IE7), even though it's COM-based, and I like that it handles the retrieval and the parsing/canonicalization of the various feed formats. However, it's unclear how I am to administer it effectively. IE7's interface is a little week if you have 400 feeds. There's no shift-select-delete support in either IE or in Outlook 2007 so I can't remove the hundreds of duplicate feeds that have appeared in the last few weeks. I've found the sync'ing solution from NewsGator to be a decent start - as an idea - but the implementation is NOT working well as it's incredibly slow and 10% of my feeds just don't sync.
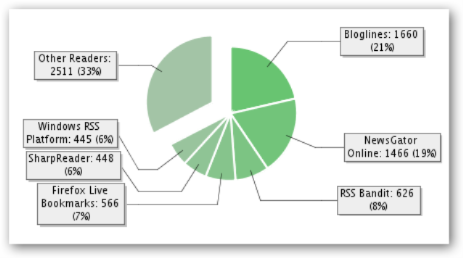 Rather than blaming NewsGator or Microsoft, I'm forced to ask, is it really this hard to keep my Feeds and Read Status sync'ed between a few computers and a few applications? Apparently it's wicked hard...this leads me to wonder if ONLINE feed reading is where its at.
Rather than blaming NewsGator or Microsoft, I'm forced to ask, is it really this hard to keep my Feeds and Read Status sync'ed between a few computers and a few applications? Apparently it's wicked hard...this leads me to wonder if ONLINE feed reading is where its at.
Apparently my readership thinks so. At least half of you are using online aggregators (or NewsGator sync'ed aggregators which includes NewsGator proper as well as FeedDemon when you're sync'ing feeds).
What do you think? Do you read your feeds online?
Do you like the one-click convenience of FEED://, or do you prefer either using FireFox's clever Feed Reader Chooser, or are you a Right Click|Copy URL|Alt-Tab|Subscribe|Paste|OK type?
About Scott
Scott Hanselman is a former professor, former Chief Architect in finance, now speaker, consultant, father, diabetic, and Microsoft employee. He is a failed stand-up comic, a cornrower, and a book author.
About Newsletter

 I'm loving Office 2007 more and more. It really does grow on you. For those of you who are having trouble finding stuff in the new Interface (and haven't discovered the automatic hotkey mapping - that's hot), there's a
I'm loving Office 2007 more and more. It really does grow on you. For those of you who are having trouble finding stuff in the new Interface (and haven't discovered the automatic hotkey mapping - that's hot), there's a 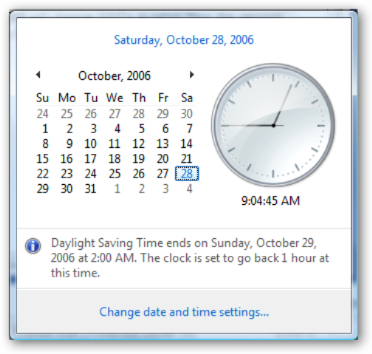 We have to change our clocks on Sunday here in the US, but if you're running a server, you need to know about this:
We have to change our clocks on Sunday here in the US, but if you're running a server, you need to know about this: When did
When did