Tracking down a Trojan
I'm not even a tenth as clever as Mark Russinovich in tracking these things down, but I got to play IT department a bit today. You're probably the IT department for your family as well. When Uncle Frank gets a virus, he calls you. In this case, I was called upon to track down a virus.
With all due respect to Russia, there's very few things that regular folks need to be visiting in a .ru domain. In this case it was SMTP traffic and there's ZERO reason anyone should be sending mail in this way.
He had ran all sorts of anti-virus, anti-spyware, and anti-malware applications and didn't find anything. A cursory glance for funky .exe's in Task Manager showed nothing obvious.
I showed up and suggested we download the three horsemen: TCPView, Autoruns, and ProcessExplorer.
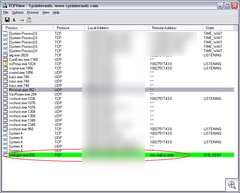
First step was to find out what process was asking for the Russian sites. TCPView to the rescue. We can see from the first screenshot that the port is being opened by winlogon.exe, the Windows NT Login Manager - certainly a legitimate executable.
There must be an evil DLL loaded inside of winlogon.exe. Next stop, Process Explorer.
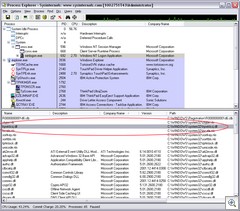 Looking at winlogon.exe within Process Explorer and changing the Lower View to show DLLs. Then I sorted by Company Name, just because it never seems that evil software writers are clever enough to include a Company Name, does it?
Looking at winlogon.exe within Process Explorer and changing the Lower View to show DLLs. Then I sorted by Company Name, just because it never seems that evil software writers are clever enough to include a Company Name, does it?
That hywklcsj.dll looks a smdge suspicious, no? Smells auto generated to me and that fact that there's no Google results for it confirmed it to me.
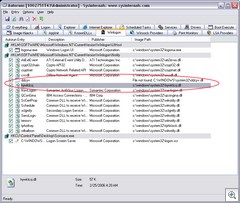 Now, Autoruns. Note the now-missing ddcyv DLL. Perhaps that was the bootstrapper that started this whole thing, but now it's run away.
Now, Autoruns. Note the now-missing ddcyv DLL. Perhaps that was the bootstrapper that started this whole thing, but now it's run away.
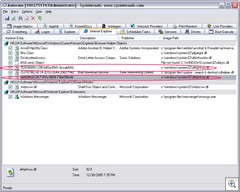 The BrowserHelperObject (BHO) section of Autoruns shows that this trojan also listens to IE and probably pops up porno ads while surfing.
The BrowserHelperObject (BHO) section of Autoruns shows that this trojan also listens to IE and probably pops up porno ads while surfing.
After cleaning all this crap up and restarting, we're clean. No funky DLLs get loaded by explorer or winlogon and no suspicious traffic tries to get our of the computer.
I'm sure this Trojan has a name, but I couldn't figure out what Google Terms I could use to find our which version it is. I suspect a Trojan.Vundo varient, but this one doesn't quite fit the profile.
About Scott
Scott Hanselman is a former professor, former Chief Architect in finance, now speaker, consultant, father, diabetic, and Microsoft employee. He is a failed stand-up comic, a cornrower, and a book author.
About Newsletter
darn, do i hate reading "news" like this about Russian "software", yet unfortunately it seems that the only kind there is :(( reasons why they do it are of course obvious (few smart guys living in 50$/mon per capita income and no outsorcing jobs around) yet it not making me feel any better :(
darn, do i hate reading "news" like this about Russian "software", yet unfortunately it seems that the only kind there is :(( reasons why they do it are of course obvious (few smart guys living in 50$/mon per capita income and no outsorcing jobs around) yet it not making me feel any better :(
Try using some good antimalware with shield capabilities like spyware doctor. Any time a program tries to install a BHO, mess with the hosts file, install an autorun program or just acts suspecious, you get prompted. This way you handle it before they plant their bomb.
abdu
Comments are closed.