Can you trust your browser extensions? Exploring an ad-injecting chrome extension
My perspective on JavaScript-based browser extensions has been far too naïve until this point. We were all burned by bad toolbars or evil ActiveX add-ons in the past, so when I run IE I run it with no add-ons enabled, or very few. However, with Google Chrome and it's sync feature, as well as its rich extension store, it's easy to add a bunch of add-ons and get them synced to other machines.
I wanted to download a YouTube video recently so I installed a "U-Tube Downloader" extension. It is highly rated, seemed legit, so I added it. It puts a nice Download button next to any YouTube video. Like greasemonkey script it was there when I needed and it, and out of sight otherwise.
I installed it and forgot about it. So, put a pin in that and read on...
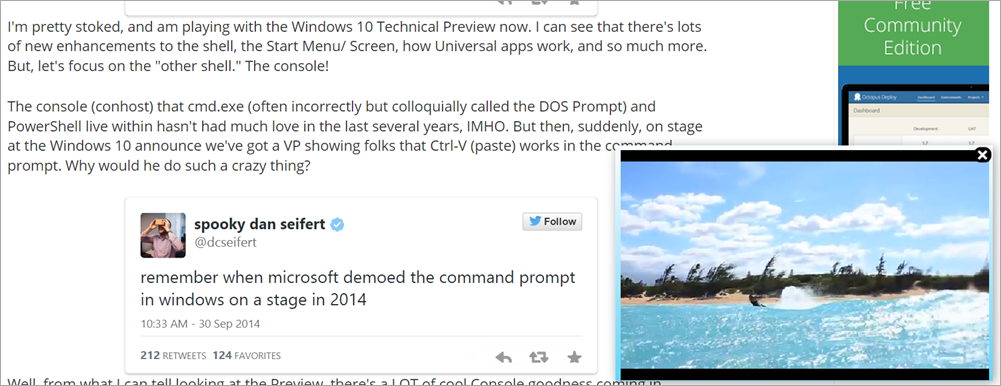
Today I was on my own site and this happened. A video slid onto my page from the right side and started playing. I was gobsmacked. I know this site, I know its code. I know my advertisers. WTH. Where is this coming from?
It's the surfing video there in the lower right corner.
First I knee-jerk emailed my advertiser asking if they were injecting this, then I pulled back and started to Inspect Element.
Looks like there's a supporting iframe, along with an injected div. That div includes JS from "vidible.tv" and the ads are picked from "panoramatech." But that's not all.
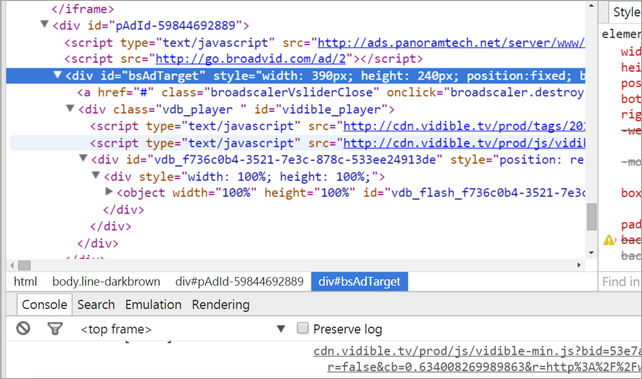
There's references to literally a half-dozen other ad-networks and then this, something called RevJet.
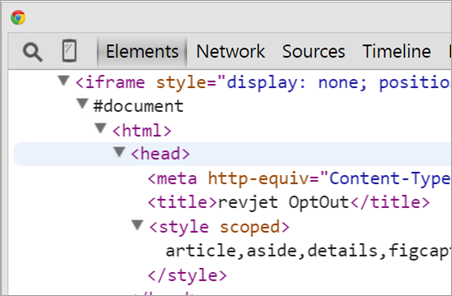
Search around and here's the first description of what RevJet is.
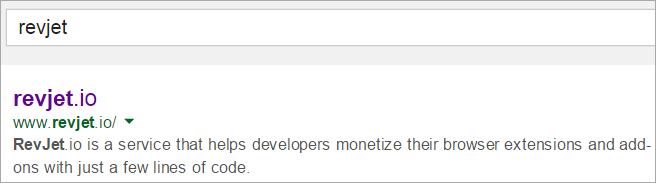
Whoa, ok, it's an extension. But which one? Grep for "Rev" in this folder C:\Users\Scott\AppData\Local\Google\Chrome\User Data\Default\Extensions and I my U-Tube one.
Nicest Ad Ever
I particularly like the comment "nicest ad ever."
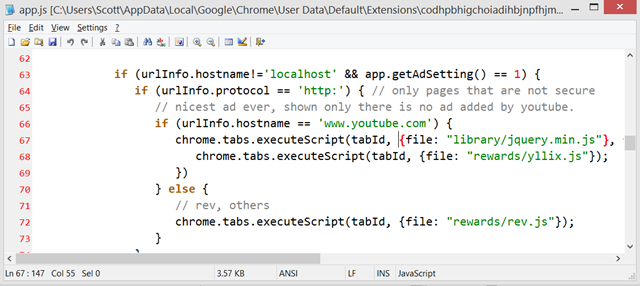
This extension also injects ads from "Yllix" when I'm on YouTube, and RevJet when elsewhere. Apparently if I set revjetoptout in my local storage, I can get around this. Very NOT intuitive. I saw no options for this extension exposing this.
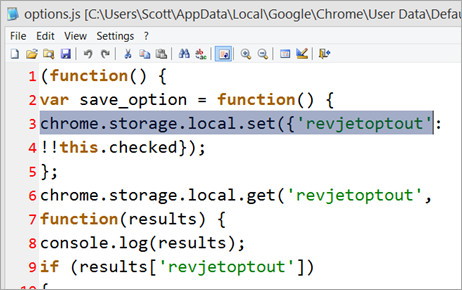
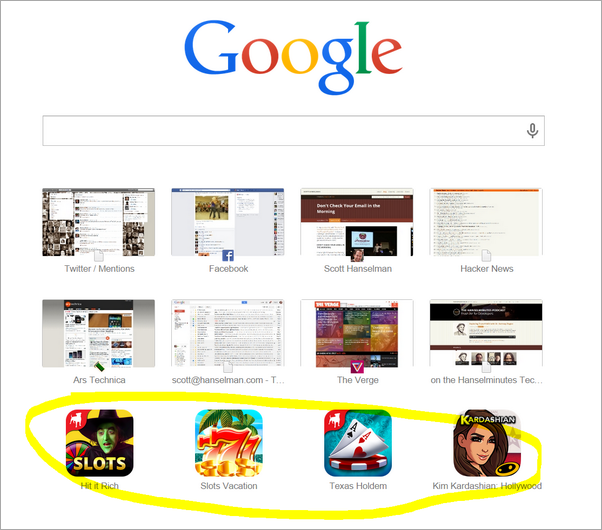
Worse yet, every once in a while, Kim Kardashian shows up in my New Tab page. Again, there's no way for non-technical relative to figure this out. And it's pretty hard for technical me to figure it out. This is deceptive at best.
Ugh.
Yes, I realize someone put work into this extension, and yes, I realize it was free. However, it wasn't clear that it was going to randomly inject ads into any website without asking. It wasn't clear that the ads were injected by this extension. There was/is no clear way for anyone without the ability to debug this to make it stop. Charge me a $1, but don't reach into webpages I visit and mess with my content without telling me.
I recommend you check out chrome://extensions/ and give each enabled one a good hard look. Consider disabling or uninstalling extensions you may have forgotten about or ones you don't explicitly trust. If you're a dev, consider reading the code within the extensions and make sure you're getting what you expect.
About Scott
Scott Hanselman is a former professor, former Chief Architect in finance, now speaker, consultant, father, diabetic, and Microsoft employee. He is a failed stand-up comic, a cornrower, and a book author.
About Newsletter
I won't install any extension that's not from Google/Chromium that has access "to all data on all websites" for this reason; injecting ads is fairly tame compared to what they could've been doing when you log in to your bank :(
This extension was adding ads for "Russian Brides" to Google Chrome and IE.
Hey Dhruv,
I'd love to talk about monetizing your Chrome extension with coupon ads. Currently, we yield our extension partners anywhere from $0.50 - $1.50 per month per daily active user through our 10,000+ merchants.
Your extension looks great so I'd like to discuss this opportunity with you further. Are you available to chat sometime this week?
Best,
<Redacted>
Senior Manager of Developer Relations
RevJet.io, a Sierra Labs, Inc. Company
3415 S Sepulveda Blvd #1250
Los Angeles, CA 90034
<redacted>@revjet.io
http://www.revjet.io/
This is how it they do it.
Zero disruption to user experience
Search ads and display ads are unnoticeable by your users.
Affiliate links (coupons) are delivered through a small, non-intrusive notification box on the top right corner of the browser window, which can be closed by the user anytime.
If you're interested I did a write up about it.
It turned out it was the addon "RSS Live Links". I used that addon for years and it never displayed ads before. But now I uninstalled it and use a similar addon. No more ads anymore.
I use this extension for this purposes https://chrome.google.com/webstore/detail/chrome-extension-source-v/jifpbeccnghkjeaalbbjmodiffmgedin
Also, they did a look at how other browsers handle their add-on ecosystem It appears to be the classic trade between human and automated curation.
Oh. That's just Disconnect.me >.>
That was enough to cause me stress and I'm pretty tech savvy. I expect my browser vendor to protect me as a consumer at least as much as they help the developer community, to which I belong. Google Chrome exposes me to unnecessary risk and until they bring some security back, it won't run on my machines.
A great way to test if a problem is cause by an extension is ctrl-shift-N to open incognito mode. By default, no extensions are allowed in incognito mode, so unless you've specifically allowed them, that will "clean off" all extensions.
You can continue to do the binary search thing by checking the box for half of them, opening incognito mode, rinse, repeat. It's quite a bit easier and less disruptive than restarting, especially if you have a bunch of existing tabs open you want to keep track of.
For me, I've hit a problem playing video more than once. Last time it was an issue with automatic HTTPS, filtering, and a CDN that couldn't deliver video (on TreeHouse). Incognito worked fine.
Just now, Amazon Prime won't stream normally, but it's fine when going incognito.
In my case, HTTPS Everywhere caused problems with both. It would be nice if websites allowed all their content as HTTPS.
-Colin
https://chrome.google.com/webstore/detail/chrome-apps-extensions-de/ohmmkhmmmpcnpikjeljgnaoabkaalbgc?hl=en
There are dozens of "infected" Google extensions. Sometimes I feel like using IE6 on Windows XP. But on the other hand: Chrome without extensions isn't a good idea either. Plus there are only few extensions that survived more than a week.
If Google won't present something innovative soon, they will get into trouble. Even if I am not one of those highly paid Google UX-Experts, I could design a better UX in a few days.
Google's ignorance with Chrome's UX and the messy extensions is really frightening.
Mozilla's extensions go through a much more rigorous vetting process. That's why it takes so long to publish and update addons to Mozilla sites. But I much prefer it.
Here's an example from the "Awesome screenshot" extension which I had to fix using my hosts file: https://gist.github.com/mvirkkunen/89f61a06819530e48b53
My hosts file currently includes the following:
127.0.0.1 ssl.google-analytics.com
127.0.0.1 cdn.extensionanalytics.com
127.0.0.1 pixel.getpaidfordata.com
127.0.0.1 tags.crwdcntrl.net
127.0.0.1 s.sitebeacon.com
127.0.0.1 collector.dataferb.com
127.0.0.1 lb.crdui.com
127.0.0.1 t.crdui.com
127.0.0.1 s821.crdui.com
127.0.0.1 s1821.crdui.com
Best part is, it renders nefarious browser extensions pretty much useless - stops the monetization path for those extensions dead in its tracks.
At least: let us not be silent and accepting about it. Discuss this, name names, and shame those who behave this way.
http://blog.chromium.org/2014/06/see-what-your-apps-extensions-have-been.html
The only extension, apart from some authentic Google extensions like Google cast, Google docs, Google keep etc., I use is AdBlock Plus! It is a boon for mankind. God bless the developers!
The one that infuriates me is secret changing of information. I installed Skype on my workstation and if you do not look closely Microsoft will change your default web settings to Microsoft's favorite choices. Skype really has nothing to do with the web, but because it is a "free", the folks in Redmond need to sneak something in on the deal.
Same thing happens with Java, Acrobat Reader and just about every other "free" product. If you didn't pay for it then YOU are the product they are selling. If you cannot figure out how they are doing that then you should be concerned.
--Monty
http://www.theregister.co.uk/2014/10/07/windows_10_data_collection/
Lovely article, I'll check my extensions right away.
The problem I think that many extensions start off clean and then in a subsequent update add in the ad injecting code and they have a mostly automated vetting process from what I can tell. That being said most of these extensions use third party code for the ad injecting so it should be relatively easy for the automated processes to detect these and remove them. You could probably report this extension and that should hopefully trigger a manual review and removal of the extension for breaching the T&Cs.
It's also worth pointing out that this isn't restricted to just chrome. Crossrider's (http://crossrider.com/developers) business model is based on this. They provide a cross browser extension building sdk which under the hood injects ad serving code into all extensions built with their sdk.
Without reading your article, I would have continued to look for the problem on my server (I discovered the inserts while I was in the admin area on one of my sites where it totally messed up the display of items).
And thanks also to other visitors for the many useful comments.
Comments are closed.
