Skip Intro - CSS3 is the new Flash
 I remember spring of 1996 when FutureSplash Animator came out. That was 16 years ago, youngsters. Our minds were blown. No one had seen a cell-based animation editor before that was so easy. This was the beginning of Flash. Macromedia bought them, and then Adobe bought them.
I remember spring of 1996 when FutureSplash Animator came out. That was 16 years ago, youngsters. Our minds were blown. No one had seen a cell-based animation editor before that was so easy. This was the beginning of Flash. Macromedia bought them, and then Adobe bought them.
Now, almost fifteen years of amazing animations, full screen fun, loading screens, auto-play music and skip intro links, Flash (and browser plugins for general use) seem to be on the way out. Proprietary binary formats are being replaced by angle brackets and curly braces.
Just when we think we've seen the limits of HTML5, CSS3 and JavaScript, another Danish 12 year old succeeds in a complete emulation of a Commodore 64 using only CSS3 or some other such magic.
But why do we hate Flash? Is it because it's a browser plugin? Is that the only reason, and even then, is it a good one? Why hate Flash? It brought us sites like this one and, of course, the greatest flash site in history.
Just to level set, take a moment and type "about:plugins" into Chrome or Firefox's address bar.
Don't fool yourself into thinking that you're browsing a plugin-free web. My Chrome instance has 15 plugins, including Google Update, Google Talk, Quicktime, Acrobat, Java, Silverlight and Flash just for starters.
In fact, today, more people have Flash or Silverlight than have Webkit. LiveScript, then Java, Flash, Silverlight, then JavaScript again, Google NaCl, and on. You've likely heard of Google NaCl (Native Client). Here's a fun quote from Matasano Security in an article called The Security Implications Of Google Native Client.
Google NaCl is, on its face, a crazy-talk idea. It’s a browser plugin that downloads native x86 code from a website and runs it on your machine. If this sounds familiar, it’s because Microsoft tried it over a decade ago with ActiveX.
You can tell how excited people are about any new Web Technology by measuring how long it takes until the obligatory "An Entire Desktop Operating System recreated in New Technology" examples show up. Ahem. I mean, seriously. Just the fact that I can Google with Bing for "Windows 7 in CSS3" and get more than one example of how to emulate Windows 7 using CSS.
However, just because you CAN do something doesn't mean you SHOULD. I prefer to use HTML5, CSS and JavaScript to create clean sites that use responsive design and progressive enhancement and are viewable as documents everywhere. I predict a clearer line will be drawn soon between sites and applications. Ironically, rather than updating a hundred apps to get the latest features, I'll instead update my browser a hundred times.
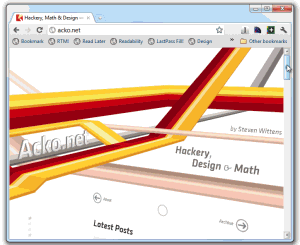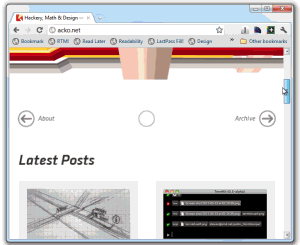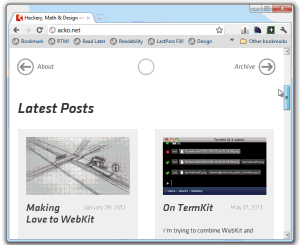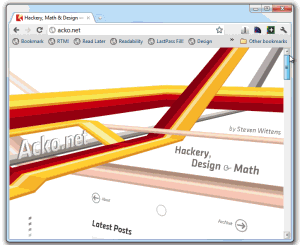
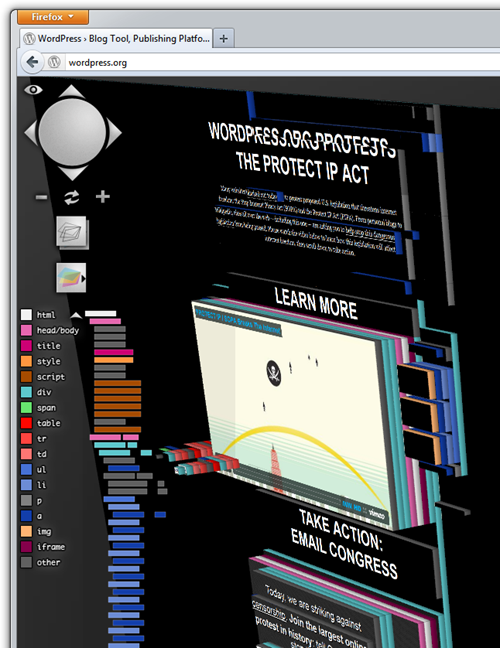
Check this amazing webkit abuse example: http://acko.net. He's truly pushing the limits of CSS3. Actually, no, it's the limits of the WebKit extensions to CSS3. As Pete Brown said, "wow, that's awesome. In the way that a circus is awesome."
UPDATE: Just to be clear, I love what Steven Wittens from http://acko.net is doing. I'm not meaning to pick on his site at all. One of the significant things worth pointing out about Steven's site is his use of media queries and CSS is all client site and works on any browser. It degrades cleanly. Yes, it's a "gaudy tech demo" but Steven backs it up with clean markup and a site that is smart enough to be functional on any browser (both past and future). His site is totally appropriate to his audience and is a good example of progressive enhancement.. I am in awe of his technical chops and encourage you to check out his content which is also excellent.
Here it is as an animated GIF. Why a gif? Because it's 100% compatible. ;) Maybe I should have used Flash.
The #1 benefit of HTML5, CSS3 and JavaScript is one thing. It's not what they can do, or how they do it. It's that they are owned by everyone. Angle brackets and curly braces are the tools of future, no question. I think we do need to ask ourselves what we want to build with those tools. HTML5, CSS3 and JavaScript of 2012 offer us all the power (and more) of FutureSplash from 1996. Let us not abuse that power and relive the sins of the father.
"The more freedom and power you have, the more you need someone to tell you what not to do." - Pete Brown
Funny thing about all this no technology. You still need a designer.
Sponsor: This week's ComputerZen feed was kindly sponsored by DevExpress. Do check out their new stuff like DXv2 and check out a free trial of their complete suite of Developer Tools. I've personally been a huge CodeRush fan for years.
About Scott
Scott Hanselman is a former professor, former Chief Architect in finance, now speaker, consultant, father, diabetic, and Microsoft employee. He is a failed stand-up comic, a cornrower, and a book author.
About Newsletter

 In August I
In August I _thumb.png)
_04ad1f12-a57d-4e39-9ced-5da75afe12e8.png)

_thumb.png)




_thumb.png)

_thumb.png)