AnkhSVN: Using Subversion within Visual Studio
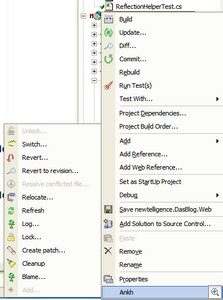 Congrats to Arild for releasing AhknSVN RC2. If you're looking to use Subversion within Visual Studio, perhaps at work or perhaps you're working on an Open Source project at SourceForge, this is the tool for you.
Congrats to Arild for releasing AhknSVN RC2. If you're looking to use Subversion within Visual Studio, perhaps at work or perhaps you're working on an Open Source project at SourceForge, this is the tool for you.
NOTE: If you do use TortoiseSVN at the same time as Ankh, do note that they are linked to Subversion 1.4, so they will upgrade your local SVN working copies. Make sure you upgrade both at the same time.
To be clear:
IMPORTANT NOTE: TortoiseSVN 1.4.0-RC1 is linked with the Subversion 1.4.0-RC4 libraries. Due to various improvements made to the working copy library, the working copy format has changed. Using TortoiseSVN 1.4.0-rc1 on any working copy created by previous versions of Subversion/TSVN will TRANSPARENTLY upgrade your working copy, which means that production-ready versions of Subversion/TSVN (1.3.x and earlier) will no longer be able to read it! Please be careful, if you use other Subversion clients (eg. the 1.3.x command line client), not to use the TortoiseSVN 1.4.x release candidate on a production working copy.
-
Download TortoiseSVN 1.4.0 RC1 here (not required to use Ankh, but DO get it if you already have a 1.3 version of Tortoise on your system)
As with all things, YMMV and back up your life.
ADDITIONAL NOTE: If you get "Unable to retrieve folder information from the server" when using VS2003 in a Web Project, you may need to go into your TortoiseSVN settings and set "use ASP.NET Hack" which tells Tortoise to use folders name "_svn" to store details rather than folders named ".svn".
About Scott
Scott Hanselman is a former professor, former Chief Architect in finance, now speaker, consultant, father, diabetic, and Microsoft employee. He is a failed stand-up comic, a cornrower, and a book author.
About Newsletter

 My
My